Why You Should Block Microsoft Legacy Authentication

Legacy authentication protocols like IMAP, MAPI, etc. can't enforce MFA, making them adversary entry points for malware attacks. Learn how to block them.
Microsoft Legacy Authentication may put your systems at risk of security compromise. Why?

The legacy authentication protocols such as SMTP, POP, MAPI, and IMAP can't enforce 2FA/MFA, making them targeted endpoints for attacks. This and other potential harms make Microsoft Legacy Authentication undesirable in a business environment.
For MFA/2FA to be effective, you need to block legacy authentication because legacy auths like SMTP, POP, IMAP, MAPI, etc. can't enforce MFA, making them entry points for attacks and adversaries.
So, in this post, we'll discuss what legacy authentication is and why you should block it to protect your business from cyber attacks and threats.
Let's get started.
What is Microsoft Legacy Authentication?
Microsoft Legacy authentication refers to the basic or old authentication protocol used to sign into a mail or other Microsoft applications and cloud services. It is an authentication request made by either:
- Older Office clients who don't have modern authentication (such as Office 2010 client), or
- Microsoft apps or client that supports legacy mail protocols/requests such as POP3SMTP/IMAP.
The Microsoft Legacy authentication protocols aren't a single protocol. They refer to anything that doesn't support or allow multi-factor authentication (MFA) or 2FA. This weak security protocol makes them vulnerable to possible unauthorized access trials and other attacks.
Many enterprises' compromising sign-in attempts are often generated from legacy authentication clients.
Legacy Authentication vs. Modern Authentication
Modern authentication protocols are those that support and allow MFA are modern authentication. Examples of modern authentication protocols are ADAL and OAuth. They're often used in Microsoft 365, Azure AD, and other Microsoft apps or cloud services.
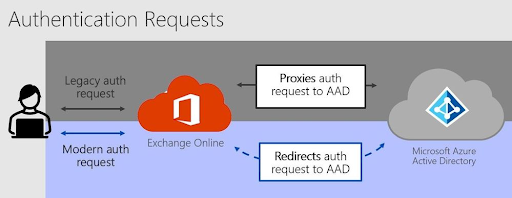
Modern authentication identity management offers safer and more secure authentication and user authorization. Users can interactively authenticate logins with a web dialog of the ID provider (such as Azure AD) rather than an app (such as Outlook) or Operating System (such as Windows). This makes handling user credentials safe, secure, and private since only the ID provider can handle the credentials and issue tokens.
In legacy authentication (also called basic authentication), users aren't protected even when they use endpoint detection and response.
Let's see the comparison of Modern Authentication vs. Legacy Authentication in the table below:
|
Legacy Authentication |
Modern Authentication |
|
A client or network protocol can't support authentication because it either lacks configuration or is incapable. |
A client or service that allows MFA/2FA. Can use OpenID Connect, SAML, and/or OAuth 2.0 authentication. |
|
Interaction is between a client and an application (not the user). The protocol sends the login (username) and password to the user's email or application rather than the user's. |
Interaction is between a client and the user (not application/service). The protocol redirects identity authentication to an ID provider, which generates tokens that the user must verify. |
|
The application/service (not the user) uses the ID (login and password) to get a login token. |
The user interacts with the ID information (login and password) to generate a token sent to the user (and not the application). |
Why Should I Block Legacy Authentication?
Answer: Legacy authentication is a basic identity authentication method with security weaknesses and is vulnerable to account breaches. It can easily allow hackers one or many 'backdoor' access routes to an organization's data.
While modern authentication understands and supports two-factor authentication (2FA) or multi-factor authentication (MFA), legacy authentication doesn't.
This is why legacy authentication is highly susceptible to automated breaches and malware attacks such as brute force, keylogging, and password spray.
Microsoft says that the trends of legacy authentication security stats are worrying. For example:
- More than 99% of password spray and more than 97% of credential stuffing attacks come from legacy authentication protocols.
- Azure AD accounts with disabled legacy authentication encounter 67% fewer compromises or attacks than those with enabled legacy authentication.
In addition, even when you've enabled a 2FA/MFA policy, a legacy authentication protocol can still allow bad actors to bypass your MFA. So, the only sure way to protect your account from attackers and malicious authentication is to block legacy protocols.
In fact, Microsoft will disable legacy authentication for all Microsoft 365 clients on October 1, 2022.
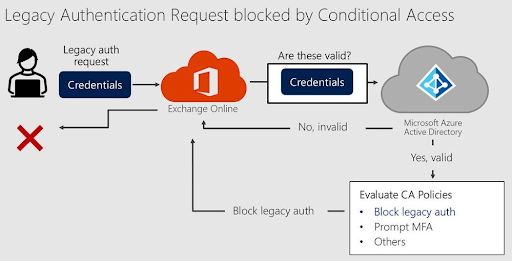
How Do I Block Microsoft Legacy Authentication?
Several methods can block legacy authentication in Microsoft 365 and related apps.
The first is blocking by default. For example, legacy auth is already blocked at tenant level if your Microsoft 365 or client has the security defaults enabled (either manually or a tenant created after October 2019).
Block legacy auth directly. You can also block legacy auth directly in your Microsoft 365, Azure Directory, or Exchange Online.
How to Block Legacy Authentication With Conditional Access Policy
The steps shown below will show you how to block legacy (basic) authentication with conditional access policy:
Step 1: Check that you have Azure AD Premium P1 license
You can only block legacy authentication through conditional access (CA) if you have Microsoft licensing with Azure AD Premium P1 or P2.
To check your license:
- Sign in to the Microsoft Azure portal.
- Go to Azure Active Directory > then Overview
- Check Azure AD premium license: P1 or P2 license.
After you've confirmed your license, you can initiate a new policy based on your license.
Step 2: Create a New (Conditional Access) Policy
You can now create a conditional access policy for the type of license you have on the Azure AD premium: license P1 or P2. A conditional policy will force-block legacy auth for all users in your directory.
You can select only a particular group of users/employees to block if you wish. But we recommend disabling legacy authentication for all apps and users.
To create a new policy, use the following steps:
- Open the Azure AD portal > go to Azure Active Directory Home
- Navigate to the Security section.
- Open Conditional Access > the open Policies.
- Select and Click New policy.
When you click on the new Policy button, you'll be required to give your policy a name.
Step 3: Input Name and Assignments
Under the "New Conditional access policy," you'll name the policy and give it assignments:
- Navigate to Name* > and give it a name (showing the policy's goal): For example, [BLOCK] Legacy authentication.
- Navigate to assignments > and Click Users and groups > choose Include > to select All users. This will block all users.
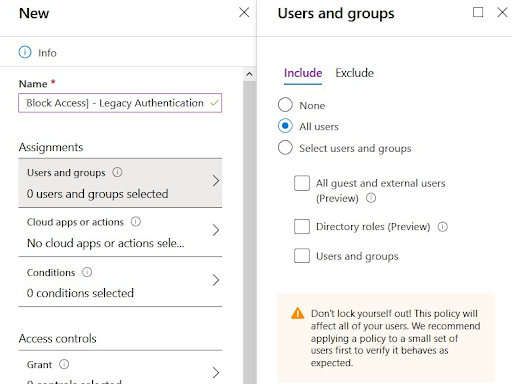
Using the conditional access policy, you can select users and groups like directory roles, guests, and external users. You'll choose the policy mode you want, depending on your desired outcome.
Step 4. Specify Cloud apps or actions
You'll specify the cloud apps and actions on the Cloud apps or actions section. This will allow you to specify clients using the conditional auth/access policy. The steps are:
- Still, on the same pane, click the 'Cloud apps' option.
- Select, Include (immediately) under cloud apps.
- Choose All cloud apps.
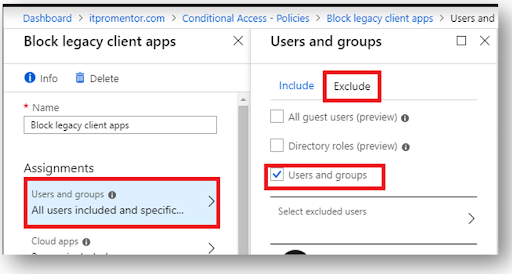
If you wish to select only particular apps, you can specify the ones you desire to use conditional access/authentication.
Step 5. Set Conditions for app use
Once you've selected the particular apps, you'll set conditions of use. Follow these steps:
- Click Conditions > select Client apps > click (or toggle) on Yes.
- Navigate to under legacy authentication clients > select mobile and desktop clients.
- Click Exchange ActiveSync clients and Other clients.
- Finally, click Done. This will set the policy as you wish.
Step 6. Grant and Enable policy
The next step is now to only grant and enables the policy you've set:
- Click Grant.
- Navigate to under control user access enforcement to block or grant access, then choose Block access.
- Below the Block access option, to the bottom, click Select.
- Below Grant, click the On switch. This selection will enable the policy you've set.
- Choose "I understand that my account will be impacted by this policy. Proceed anyway."
- Click Create and exit.
Congratulations! You've blocked Legacy Authentication using the Conditional Access Policy. You'll see this policy in your Conditional Access policies list.
Don't be worried if it doesn't show up immediately because it can take up to 24 hours.
Conclusion
That's why you should disable legacy authentication and how to do it with Conditional Access.
This setting will help you secure your data from attacks and obvious malicious authentication requests.
We hope the above methods helped you block legacy auth users and apps.
Now, we'd like to turn it to you.
If you have any questions or suggestions, feel free to contact our customer care team.
Looking for more tips? Check out our other guides, tips, tricks, troubleshooting, reviews, and more in the Softwarekeep Blog and our Help Center! You'll find a wealth of information and solutions to your tech problems.
Also, sign up for our newsletter and access our blog posts, promotions, and discount codes early.
Recomended Articles
» Mobile Device Management (MDM) for Microsoft 365: Ultimate Guide
» How to Keep Your Data Safe When Using Microsoft Office 365
» Step by Step Guide to Set Up Office 365 Business eMail
» Differences Between Microsoft 365 vs. Google Workspace
» How To Fix Keyboard Typing Backward on Windows 10 and 11